D39yp714n ▲▲▲
39yp714n ▲▲▲ is a misc Challenge with 400 points and 0 solved
I got a hint after the competition, then I was able to solve it .
After downloading the challenge you got a defected png called fixed.png
try to open it ,
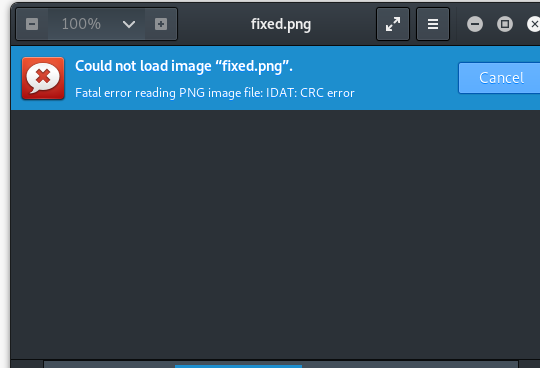
you’ll get this, it can’t be identified as png.
Before checking it, let’s try to look to the metadata by exiftool, maybe we get the flag or get some help.
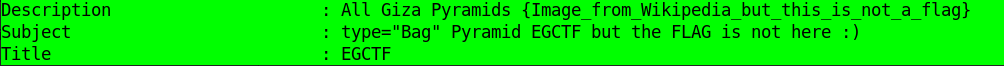
we just got a small description of the image and a message telling us the flag is not here .
so lets continue with pngcheck .
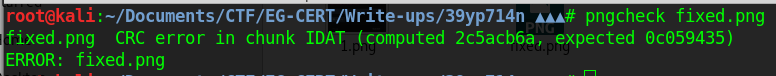
i really didn’t understand what is that error means .
so i take all the error and searched for it on google .
I found a write-ups for challenges with the same problem .
I read one of them and finally I understood what was that mean .
the headers that identify the file as png were in the wrong positions with a wrong length for some of them .
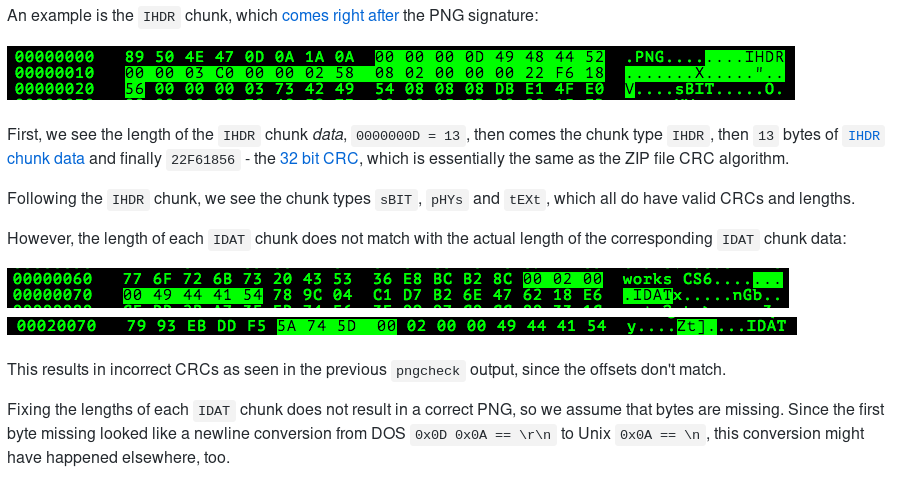
so we have to fix the headers .
so you can read more about png headers and you can make your own fixing tool , or you can search for a fixing tool as what i did , or you can easily put the png to any photoshop and it’ll fix the image .
i found png header fixer
after fixing the png i got this photo of Giza pyramids as in the description .

i know what are you thinking about , the flag is the words in the sand .
but believe me, I spent the last 2 hours in the competition trying to read it, and I couldn’t .
what about the data matrix, lets see what is the hidden data on it?
I used an online tool to check it, and I found a hint.
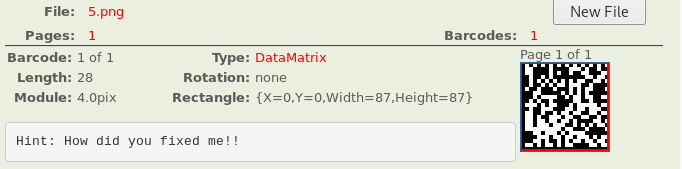
” Hint : How did you fixed me!! “
then I tried to get any more data from the pixels of the data matrix, but there was nothing more .
Usually any challenge contains a step that contains a change of the source of the file , i do xor to the old source and new one , but i didn’t do that here .
and that was the hint i got after the completion ,” oldcrc ^ newcec “ .
so i managed to try the xor and i used this script :
new = open("output.png").read()
old = open("fixed.png").read()
newhex = ["{:02x}".format(ord(c)) for c in new ]
oldhex = ["{:02x}".format(ord(c)) for c in old ]
flag =[]
for i in range (len(newhex)) :
x = int(newhex[i], 16)
y = int(oldhex[i], 16)
if ( y^x != 0):
flag.append(chr(y^x))
print ''.join(flag)
and we got the flag .
after handling it
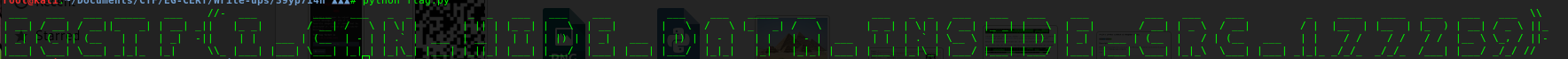
EGCTF{I_CAN_HIDE_DATA_INSIDE_CRC_177259}
not : the number at the end changes depending on your team