STRINGS
Strings is a reverse challenge
After downloading it in a Linux environment, and running file command I got this output
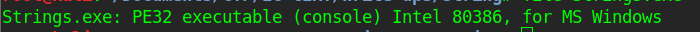
yup it’s PE32 , mmm
you start to think of ida or ghidra, but I think of Olly

but before moving to Olly, the name of the challenge is very interesting, so I tried to run the strings command on it and I got this
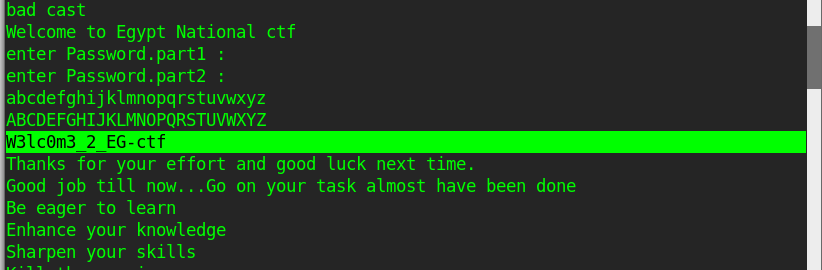
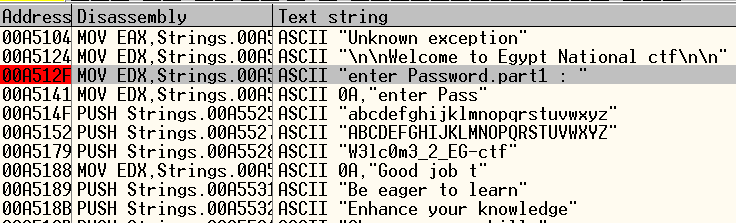
W3lc0m3_2_EG-ctf
very interesting it seems to be the flag, so I tried to submit it, but it wasn’t that easy .
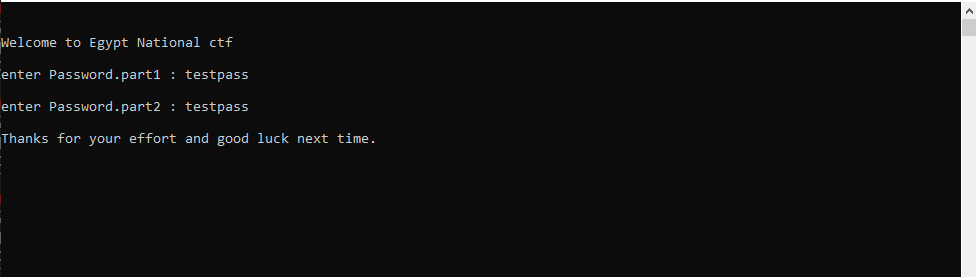
time to test the challenge .
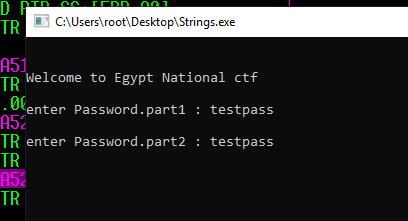
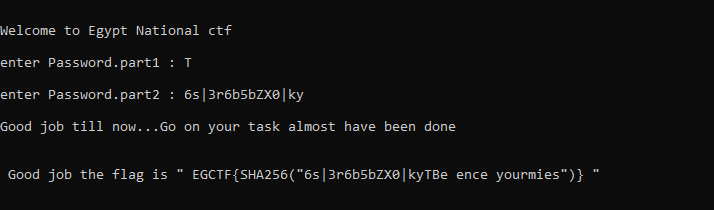
after opening the exit it asked for password part1 then asked for part2 I tried W3lc0m3_2_EG-ctf and many passwords in different ways, but it always shows try the message of wrong password .
now we know the target is to enter the right 2 parts of the password to get the flag.
lets load it to olly .
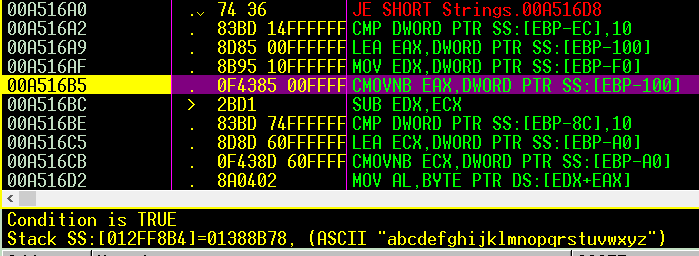
I stared to search for the strings that had appeared on the test .
I found the message to the first part, so I put a breakpoint and moved to it .
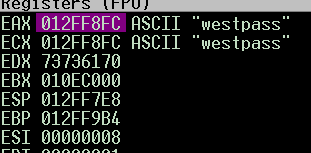
thin I put the first part as : “testpass”
that I followed the code to see what happens to the password.
Nothing interesting happened until this point .
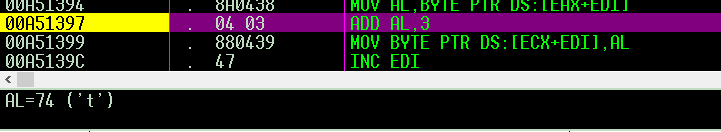
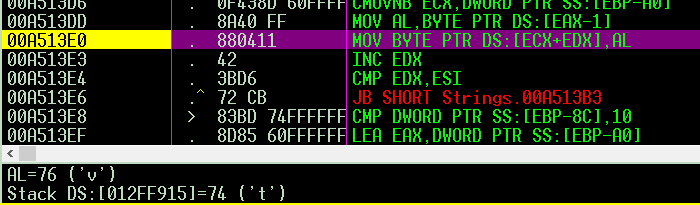
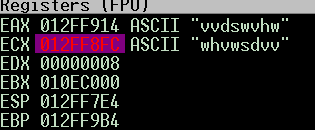
it adds 3 to “AL” where the first char of my password, which is ‘t’ so it’ll become ‘w’
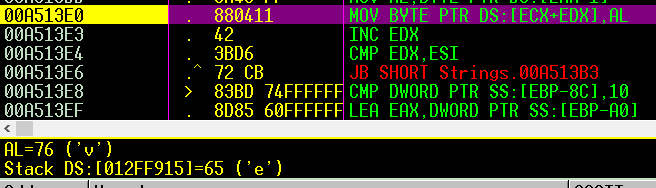
then the loop continued to add 3 to all “testpass” chars, so it becomes “whvwsdvv” .
1 - so we have to sub 3 to get
I expected it will ask for the part 2 after that, but it starts to do another operation on the encoded password .
it started to put the encoded pass in reverse order and compare the position with the my plan password chars .
so the password changed from “whvwsdvv” to “vvdswvhw”
2 - so we have to put the pass in reverse order
Finally the operation on part 1 ended, and asked for the part 2.
the fun is about to start .

Also, I but “testpass” as part2 .
followed the instructions
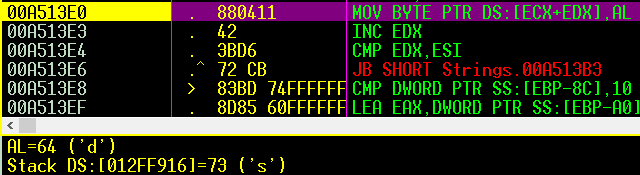
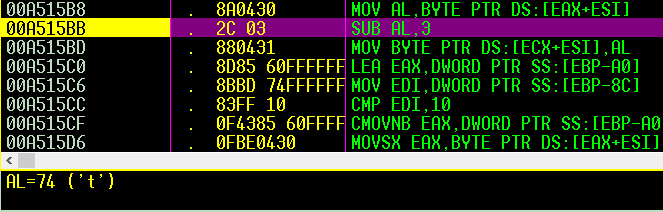
on the opposite of part1 here it sub 3 from the password chars
3 - so you just add 3 to this step
so i expected the value of “t” will be “q” , but it changed to “k”
i got unexpected values for all chars except ‘ a ‘ it become ‘ ^ ‘ as expected .
there was a strange condition comparing the all chars after the encoded one till z with a.. z
so my expectation to the code was
if passchr-3 in a to z or A to Z :
do the next step of encodeing .
else :
i really didn't know
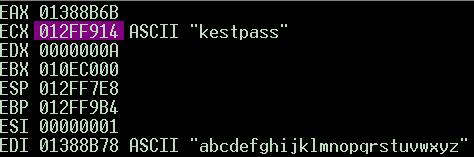
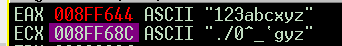
so i tried the password ‘123abcxyz’
I got ‘123abc’ as ‘./0^_`’ as it was expected
so in else it keeps the encoded char whit no changes .
and i got ‘xyz’ as ‘gfe’
LOL it become very obvious
the alphabet is in reverse order, starting from ‘e’ to ‘z+3’ .

4- you have to revise the alphabet after encoding
or just follow the image above to get to part two
Now the operation on part 2 ended time to know the password .
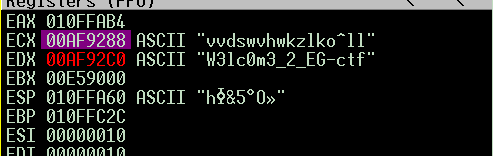
back to “testpass” :
after encoding the parts it content together and compardto the password .
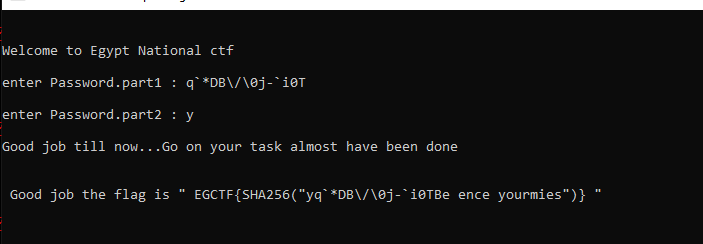
I was right “W3lc0m3_2_EG-ctf” was the password.
the funny is that, the code doesn’t check the length of any part .
time to decode it.
write a script to get the two passwords .
this will be the output for decoding all the password “W3lc0m3_2_EG-ctf” with both ways .

remember: part1 pass is from right to left
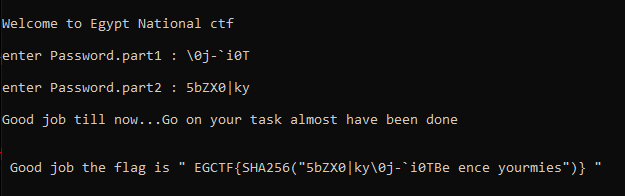
now time to check our solution .
wow, it’s right, we got the flag : EGCTF{a1b2f5bf436b46bb092239d9e0ff86718eaf74cca1bfa6d43ad554000cacb2c7}
but wait, this also is a valid flag : EGCTF{d3de9d031bf1edf83da8ac211c4fe10fb805f6871b0dd49d8489c8fd0a961ab4}
Also, this one is valid : EGCTF{c7d70dfe682b42a73db335f00f33029e19864be42c16f6b65fd823a66affa8db}
remember the length of any part is not important, what is important is to equal the “W3lc0m3_2_EG-ctf” at the end